Can you truly harness the power of your Raspberry Pi from anywhere in the world, even when hidden behind the protective veil of a firewall? The answer is a resounding yes! With the right knowledge and freely available tools, you can unlock secure remote access, transforming your little computer into a versatile tool accessible from wherever your digital journey takes you.
The modern digital landscape demands flexibility and control. Whether you're a seasoned tech professional, an enthusiastic hobbyist, or simply someone curious about expanding their technological horizons, the ability to remotely access your Raspberry Pi is a game-changer. It allows you to monitor projects, manage data, or simply tinker with your setup from the comfort of your couch, a coffee shop, or even across continents. But what if your Raspberry Pi resides behind a firewall, a common security measure that restricts external access? This is where the real challenge and the real opportunity begins.
This article is designed to be your comprehensive guide to achieving exactly that: secure, remote access to your Raspberry Pi, regardless of firewalls and routers, all without breaking the bank. We'll delve into the practical steps, explore the necessary tools, and demystify the concepts, empowering you to take control of your digital infrastructure.
The Raspberry Pi
The Raspberry Pi, with its compact size and versatility, has revolutionized the way we interact with technology. This tiny computer can be transformed into a media server, a home automation hub, a learning tool, or even a portable gaming console. But its true potential is unleashed when you can access it remotely. Imagine the possibilities: updating software, troubleshooting issues, or monitoring sensors from anywhere with an internet connection. This level of accessibility opens doors to unparalleled convenience and control.
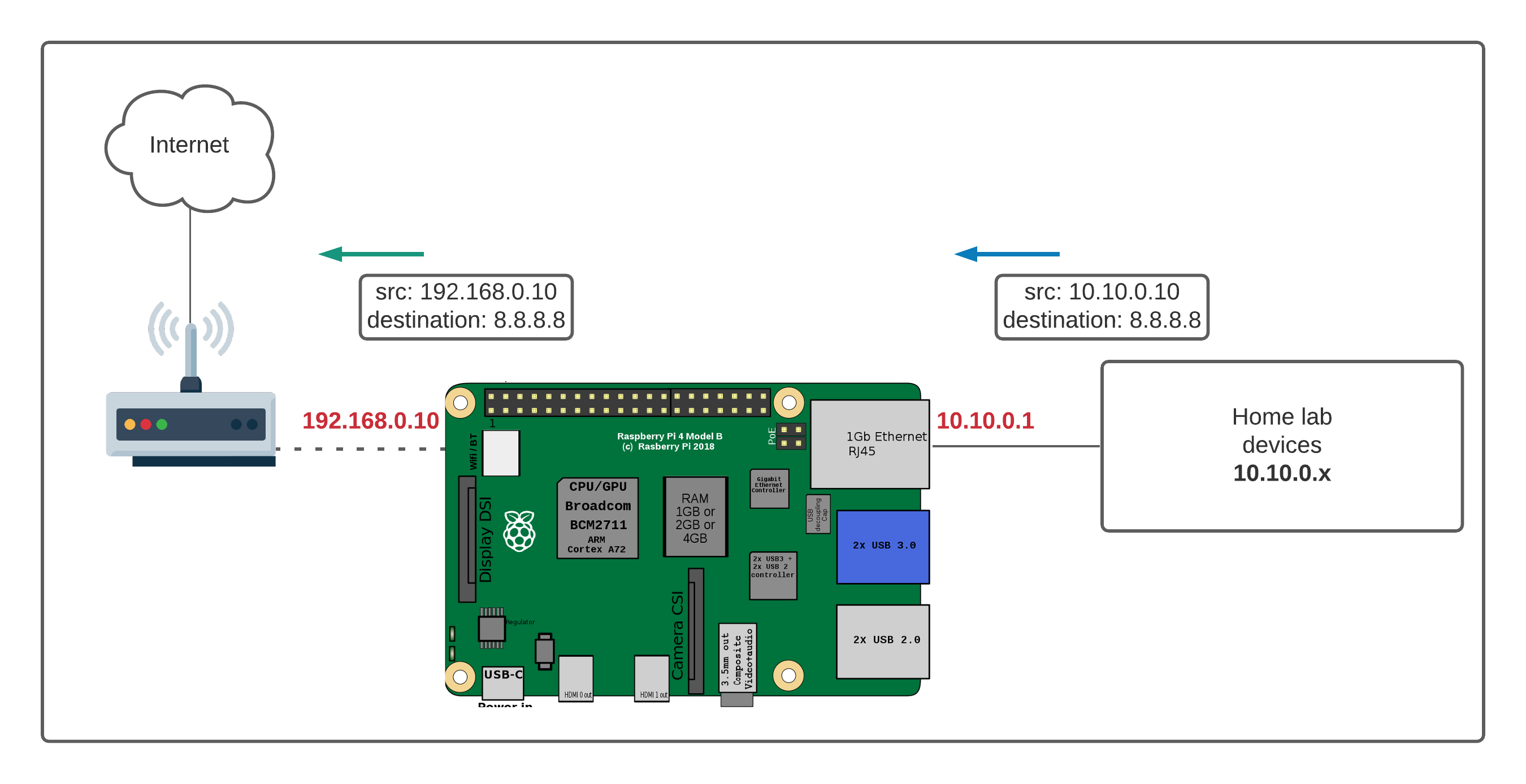
The Firewall Conundrum
Firewalls, a crucial component of network security, act as a barrier between your network and the outside world. They scrutinize incoming and outgoing traffic, blocking potentially malicious connections and protecting your devices from unauthorized access. While essential for security, firewalls can also present a hurdle when you want to remotely access a device like your Raspberry Pi. Standard remote access methods often rely on direct connections, which firewalls are designed to prevent.
Overcoming the Obstacles
The good news is that several ingenious methods exist to circumvent the firewall challenge and establish secure remote access to your Raspberry Pi. These approaches typically involve techniques like SSH tunneling, VPN solutions, and cloud-based services. Each method has its own strengths and weaknesses, and the best choice will depend on your specific needs and technical expertise.
Key Concepts and Technologies
Before we dive into the how-to, let's familiarize ourselves with some core concepts:
- SSH (Secure Shell): A cryptographic network protocol that allows you to securely access and manage remote devices. It provides a secure channel for command-line interaction, file transfer, and other network services.
- Firewall: A security system that monitors and controls network traffic based on a set of rules. It acts as a barrier, protecting your network from unauthorized access.
- Router: A device that forwards data packets between computer networks. In a home network, the router typically acts as a firewall, NAT (Network Address Translation) device, and Wi-Fi access point.
- NAT (Network Address Translation): A process that allows multiple devices on a private network to share a single public IP address. This is commonly used in home networks.
- Reverse SSH Tunneling: A technique that creates a secure connection from the Raspberry Pi (behind the firewall) to a server with a public IP address. This allows you to access the Raspberry Pi via the server.
- VPN (Virtual Private Network): A technology that creates a secure, encrypted connection over a public network, like the internet. This allows you to access your Raspberry Pi as if you were on the same local network.
- ngrok, Cloudflare Tunnel: Cloud-based services that create secure tunnels to your Raspberry Pi, allowing you to access it from anywhere without complex configuration.
Tools of the Trade
Fortunately, gaining remote access to your Raspberry Pi doesn't require a costly investment. The tools you need are readily available and often free to use. Here are some key players:
- SSH Client (e.g., PuTTY, OpenSSH): These tools enable you to connect to your Raspberry Pi via SSH. PuTTY is popular on Windows, while OpenSSH is typically pre-installed on Linux and macOS.
- ngrok/Cloudflare Tunnel (Free Tier): These cloud services provide secure tunnels to your Raspberry Pi, allowing you to access it from anywhere. Their free tiers are often sufficient for basic use.
- VNC Client (e.g., RealVNC Viewer, TightVNC): If you want a graphical interface, VNC clients allow you to remotely view and control your Raspberry Pi's desktop.
- A text editor (e.g., nano, vi, Notepad++): For editing configuration files on your Raspberry Pi.
Step-by-Step Guides to Remote Access
Now, let's roll up our sleeves and dive into the practical steps for setting up remote access. We'll cover several popular methods, each with its advantages and disadvantages.
Method 1
Reverse SSH tunneling involves establishing a secure connection from your Raspberry Pi (behind the firewall) to a server with a public IP address. This allows you to access your Raspberry Pi via the server. This method requires a server with a public IP address, which can be a virtual private server (VPS) or another computer you control.
- Set up the server: Configure a server with a public IP address. This could be a VPS provider like DigitalOcean, AWS, or Google Cloud Platform. Ensure that SSH access is enabled on the server.
- Install an SSH client on your Raspberry Pi: Most Raspberry Pi operating systems come with OpenSSH pre-installed. If not, install it using the command: `sudo apt update && sudo apt install openssh-client`.
- Establish the reverse SSH tunnel: On your Raspberry Pi, run the following command, replacing `[user]` with your username on the server, `[server_ip]` with the server's IP address, and `[local_port]` with the port you want to use on your local machine to access the Pi.
`ssh -R [local_port]:localhost:22 [user]@[server_ip]`
This command creates a tunnel from the server back to your Raspberry Pi, listening on the specified port on your server and forwarding traffic to port 22 (SSH) on your Raspberry Pi. - Access your Raspberry Pi: From your local machine (e.g., your laptop), connect to the server using SSH, but specify the local port you configured for the tunnel. For instance:
`ssh -p [local_port] [user]@[server_ip]`
This will connect you to your Raspberry Pi via the server and the reverse SSH tunnel.
Method 2
ngrok is a cloud service that simplifies the process of creating secure tunnels to your Raspberry Pi. It eliminates the need for a public IP address or complex firewall configuration. Here's how to use it:
- Sign up for an ngrok account: Create a free account at ngrok.com.
- Download and install ngrok on your Raspberry Pi: Follow the instructions on the ngrok website to download and install the ngrok client on your Raspberry Pi.
- Connect your Raspberry Pi to ngrok: Run the following command, replacing `[your_auth_token]` with your ngrok authentication token (found in your ngrok dashboard):
`./ngrok tcp 22`
This command creates a secure tunnel to port 22 (SSH) on your Raspberry Pi. - Access your Raspberry Pi: ngrok will provide you with a public URL and port number. Use this information to connect to your Raspberry Pi via SSH. For example, if ngrok gives you the address `0.tcp.ngrok.io:12345`, you would connect using:
`ssh pi@0.tcp.ngrok.io -p 12345`
Replace "pi" with your Raspberry Pi username.
Method 3
Cloudflare Tunnel offers a similar functionality to ngrok, providing a secure tunnel to your Raspberry Pi through Cloudflare's global network. It also leverages Cloudflare's security features.
- Sign up for a Cloudflare account: Create a free account at cloudflare.com. You'll also need a domain name that is managed by Cloudflare.
- Install and configure Cloudflare Tunnel on your Raspberry Pi: Follow Cloudflare's instructions to install the `cloudflared` client and configure it for your domain. This usually involves creating a tunnel and generating an authentication token.
- Create a tunnel for SSH: Within the Cloudflare dashboard, create a tunnel that forwards traffic from a subdomain (e.g., `ssh.yourdomain.com`) to port 22 on your Raspberry Pi.
- Access your Raspberry Pi: Use the subdomain you configured (e.g., `ssh.yourdomain.com`) and your usual SSH username to connect to your Raspberry Pi.
`ssh pi@ssh.yourdomain.com`
Method 4
Another option for creating secure remote access is to set up a VPN server on your home network. This will allow you to connect to your home network securely and then access your Raspberry Pi from within your home network.
- Set up a VPN server on your Raspberry Pi: Install and configure a VPN server, such as OpenVPN or WireGuard, on your Raspberry Pi. You'll need to generate certificates and configure user access.
- Connect to the VPN: From your remote device (e.g., your laptop or smartphone), connect to your VPN using a VPN client.
- Access your Raspberry Pi: Once connected to the VPN, you can access your Raspberry Pi using its local IP address, as if you were on your home network.
Securing Your Remote Access
While these methods provide access to your Raspberry Pi, it's crucial to prioritize security. Here are some key steps to take:
- Change the default password: Immediately change the default username and password for your Raspberry Pi. Use a strong, unique password.
- Use SSH keys: Instead of passwords, use SSH keys for authentication. This is more secure and convenient.
- Enable two-factor authentication (2FA): If possible, enable 2FA for SSH access to add an extra layer of security.
- Keep your software updated: Regularly update your Raspberry Pi's operating system and installed packages to patch security vulnerabilities.
- Firewall rules: Implement firewall rules on your Raspberry Pi to restrict access to only the necessary ports and IP addresses.
- Monitor your logs: Regularly review your SSH logs and other system logs for suspicious activity.
Choosing the Right Method for You
The best method for remote access depends on your technical skills, your network configuration, and your specific needs. Here's a quick comparison:
| Method | Pros | Cons | Complexity | Use Case |
|---|---|---|---|---|
| SSH Tunneling (Reverse SSH) | Secure, flexible, no reliance on third-party services | Requires a server with a public IP address, more complex setup | Moderate | Advanced users, situations where you need a dedicated server |
| ngrok | Easy to set up, no port forwarding required, free tier available | Reliance on a third-party service, limited free tier features | Easy | Quick and easy remote access, ideal for beginners |
| Cloudflare Tunnel | Secure, leverages Cloudflare's infrastructure, free tier available | Requires a domain name managed by Cloudflare, slightly more complex setup | Moderate | Secure and reliable remote access, suitable for users familiar with Cloudflare |
| VPN | Provides secure access to your entire home network, encrypted connection | Requires setting up a VPN server, can be more complex to configure | Moderate to Advanced | When you need access to multiple devices on your home network, or for additional security |
Table data is sourced from the provided text and is presented to clarify the process.
Troubleshooting Common Issues
Setting up remote access can sometimes be tricky. Here are some common issues and their solutions:
- Connection refused: This typically means the SSH server is not running on your Raspberry Pi or the firewall is blocking the connection. Check your Raspberry Pi's SSH configuration and ensure the firewall allows SSH traffic.
- Authentication failure: This usually indicates an incorrect username or password. Double-check your credentials and consider using SSH keys.
- Network connectivity issues: Ensure your Raspberry Pi has an active internet connection. Check your router settings and firewall configuration.
- ngrok/Cloudflare Tunnel not working: Double-check your ngrok or Cloudflare configuration, including the authentication token and tunnel settings. Make sure the service is running on your Raspberry Pi.
Remember to consult the official documentation for your chosen method and search online for solutions to specific error messages.
Beyond SSH
While SSH provides a powerful command-line interface, you might want a graphical interface for remote access. This is where VNC (Virtual Network Computing) comes into play.
VNC allows you to remotely view and control your Raspberry Pi's desktop. It's particularly useful for interacting with applications and performing tasks that require a visual interface. Popular VNC servers for Raspberry Pi include RealVNC Server and TightVNC Server.
To set up VNC access:
- Install a VNC server on your Raspberry Pi.
- Configure the VNC server with a password.
- Open the VNC port (usually 5900) in your firewall.
- Install a VNC client on your remote device (e.g., RealVNC Viewer).
- Connect to your Raspberry Pi using the VNC client, specifying the IP address and port number.
Alternative Desktop Access: RDP (Remote Desktop Protocol) offers another option, providing potentially better performance than VNC in some instances. However, RDP setup on Raspberry Pi can be slightly more involved.
The Power of Automation
For those managing multiple Raspberry Pis, automation becomes essential. Tools like Ansible and shell scripts can streamline the process of configuring, updating, and managing your fleet remotely.
Here's how:
- Ansible Playbooks: Define tasks for common operations, such as installing software, configuring network settings, or updating security configurations.
- Scripting: Write scripts to automate specific tasks and then execute them remotely.
- Centralized Management: Establish a central server to manage your Raspberry Pis through SSH, deploying updates and configurations in a consistent manner.
The ability to automate tasks saves significant time and effort, ensuring that your Raspberry Pis are consistently configured and up-to-date.
Real-World Applications
The ability to remotely access your Raspberry Pi has countless real-world applications. Here are just a few examples:
- Home Automation: Control smart home devices, monitor sensors, and manage your home security system from anywhere.
- Media Server: Access your media library, stream movies, and listen to music while on the go.
- Data Logging and Monitoring: Collect data from sensors, monitor environmental conditions, and track system performance remotely.
- Software Development: Test and debug software projects on your Raspberry Pi from your development environment.
- Education and Learning: Experiment with coding, learn about electronics, and explore the capabilities of the Raspberry Pi from anywhere.
- Remote Robotics and IoT projects: Control and monitor robotics projects.
The Future is Remote
The ability to remotely access your Raspberry Pi is no longer a luxury; it's a necessity in today's interconnected world. By mastering the techniques described in this guide, you're equipping yourself with a valuable skill set that will empower you to control your digital life, explore new technologies, and push the boundaries of what's possible.
With the right approach, overcoming firewalls and routers is no longer a barrier, it's a challenge easily overcome. The power of remote access is at your fingertips. It's time to connect, explore, and unleash the full potential of your Raspberry Pi!
This journey into remote access provides the freedom to interact with your devices, from anywhere in the world, with full control and security.