Can you remotely access and control your Internet of Things (IoT) devices from anywhere in the world, securely and without incurring hefty costs? Mastering remote SSH login for your IoT servers is not just a convenience; it's a necessity for efficient management, troubleshooting, and development.
The modern landscape of IoT demands constant vigilance, seamless accessibility, and robust security. The ability to connect to your devices, regardless of their physical location, is paramount. This guide serves as a comprehensive exploration of free and effective remote SSH login solutions, designed to empower you to take control of your IoT infrastructure. We'll navigate the complexities of remote access, providing you with the knowledge and practical strategies to ensure secure and efficient management of your devices. Forget the constraints of on-site presence or the complexities of VPN setups. The world of IoT device management can be streamlined, cost-effective, and surprisingly simple.
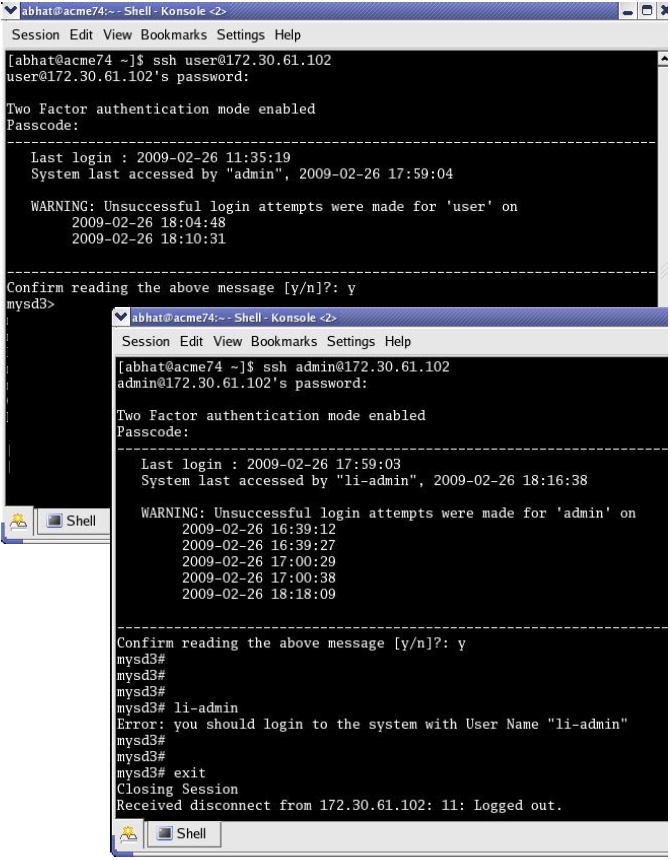
Let's delve into the core of the matter: What exactly is remote SSH login, and why is it so vital for IoT devices? SSH (Secure Shell) is a cryptographic network protocol that provides a secure channel for communication over an unsecured network. It facilitates a secure connection to a remote server, allowing you to execute commands, transfer files, and manage your device as if you were physically present. In the realm of IoT, this capability transforms the way you interact with your devices. Imagine updating firmware, monitoring sensor data, or troubleshooting issues without ever leaving your desk. This translates to significant time and cost savings, as well as increased responsiveness to potential problems.
The benefits extend far beyond convenience. Remote SSH access provides a powerful toolkit for managing your IoT devices. You can easily monitor their performance, diagnose and resolve technical issues, and perform critical maintenance tasks. This also makes it possible to rapidly prototype and test new functionalities on your devices. Furthermore, secure remote access is crucial in environments where physical access is limited or impractical, such as in remote locations or industrial settings. You can also minimize downtime as you can troubleshoot and resolve any issues from your home.
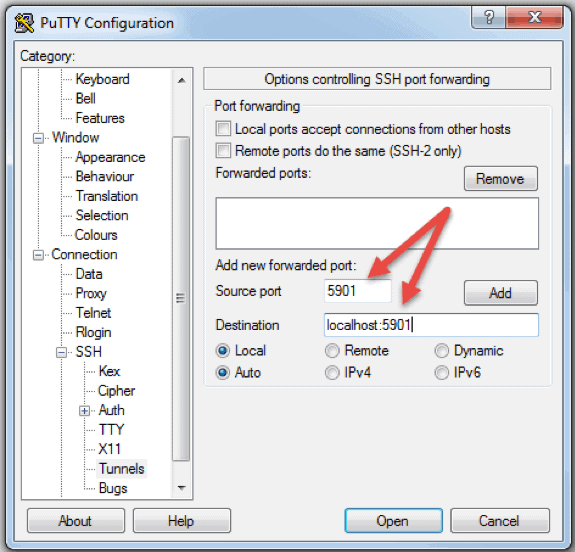
However, the question arises: how do you achieve secure remote SSH login, and what are the tools available to make this possible? While complex, there are a number of strategies, starting with choosing free open-source software solutions. The good news is that OpenSSH, a widely adopted and freely available implementation of the SSH protocol, offers a robust and secure foundation for remote access. This software allows you to establish encrypted communication channels over computer networks, ensuring the confidentiality and integrity of your data. This also means that your data is protected while it is transferred between your device and the server. Furthermore, many cloud providers provide free SSH access, which can be easily configured.
Another important point to consider is the operating system of your IoT devices. If your device is not Ubuntu Linux-based and you want to install and configure an SSH server, SSH clients, and SSH public/private keys for remote SSH access, you will need to follow a few steps. Firstly, install an SSH server on your device. This can be done using the appropriate package manager for your device's operating system. Once the server is installed, you'll need to configure it by setting up user accounts and specifying access permissions. Next, configure SSH clients on the machines from which you intend to remotely access your devices. This will allow you to connect to your IoT devices from any location. Finally, generating and managing SSH keys is essential for a secure connection. Use a public key to verify your identity and a private key to unlock the connection.
One of the primary challenges of remote SSH login lies in security. Since you are exposing your devices to the internet, it's essential to take the appropriate security measures. Always use strong, unique passwords, and regularly change them. Disable password-based authentication entirely, and instead rely on SSH key-based authentication. This approach is significantly more secure, as it eliminates the risk of brute-force attacks. In addition to this, configuring a firewall to restrict access to the SSH port (typically port 22) is also a good idea. Only allow SSH connections from trusted IP addresses or IP ranges to protect your network. It is important to regularly monitor logs for any suspicious activity and take immediate action if any security breaches are identified. Consider using a VPN (Virtual Private Network) for an additional layer of security.
Let's explore some practical tips to ensure a secure and efficient remote SSH login experience.
- Implement SSH Key-Based Authentication: Ditch password-based logins entirely. Generate a strong key pair (public and private) and use the private key to authenticate. This prevents brute-force password attacks.
- Configure a Firewall: Limit access to the SSH port (usually port 22) by only allowing connections from trusted IP addresses or ranges.
- Use Non-Standard SSH Port: Change the default SSH port to a less common one. This can help to reduce the number of automated attacks.
- Regularly Update and Patch: Keep your SSH server and all associated software up to date to address any security vulnerabilities.
- Monitor Logs: Regularly check your SSH logs for any suspicious activity.
- Use Fail2Ban: Implement Fail2Ban to automatically ban IP addresses that repeatedly attempt to log in with incorrect credentials.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security by requiring a second verification method, such as a code from an authenticator app.
- Disable Root Login: Do not allow root users to log in directly. Instead, use a regular user account and then elevate privileges using sudo.
- Limit Login Attempts: Configure your SSH server to limit the number of unsuccessful login attempts before locking out the user.
One compelling benefit of this methodology is the ability to rapidly prototype and deploy new features. The moment you create a small improvement for your device, it can be accessed instantly, which allows you to get a fast and reliable experience. Start remote prototyping from day one, without having to design and operate the IOT infrastructure. This significantly reduces the time spent on physical interactions with devices, and allows you to perform actions remotely.
The selection of tools available is wide and varied, but understanding your needs can lead to a more tailored solution. Torizon's remote access feature, for example, is specifically designed as an ideal field debugging solution. You can debug and configure your remote IoT devices as if they were within reach of your hands. Consider the operating system, devices resource constraints, and your desired level of security to arrive at the best option for your use case. There are other alternatives, but this particular one offers a comprehensive package for managing IoT devices.
With remote SSH connection, the possibilities expand exponentially. It's a powerful tool that unlocks numerous benefits for IoT device management, and makes it possible for you to unlock the full potential of your IoT ecosystem. Now is the time to take control of your devices and experience the freedom and efficiency of remote SSH login.