Are you struggling to manage your Internet of Things (IoT) devices securely and efficiently from a distance? The ability to remotely access and control your IoT devices via secure methods like SSH (Secure Shell) is not just a convenience; it's becoming a necessity in today's interconnected world.
The digital landscape is evolving at an unprecedented pace, and with it, the challenges of managing remote devices. The proliferation of IoT devices has created a complex ecosystem where secure, reliable access is paramount. This article delves into the realm of remote access solutions for IoT devices, focusing on SSH, web-based interfaces, and various tools and strategies that ensure both functionality and security. We'll explore the intricacies of accessing devices behind firewalls, the benefits of web-based control, and the importance of understanding the fundamental concepts to make informed decisions. From the basics of SSH to the practical implementations of remote access protocols, this is your guide to the tools and techniques necessary to navigate this new paradigm.
Let's examine the underlying principles and practical applications of this approach, focusing on the key aspects of ensuring secure and efficient remote management. We'll begin by establishing a solid foundation of knowledge, covering the essential protocols, methods, and best practices that form the bedrock of successful remote access implementation. The objective is not only to provide the knowledge necessary to securely access your devices, but also to empower readers to adapt to the dynamic demands of the connected world.
Before we delve into the specifics, it is important to clarify a very basic but crucial aspect: Why is remote access to IoT devices necessary? In the realm of IoT, remote access capabilities are essential, driving efficiency and streamlining operations. The advantages are multifaceted, extending beyond mere accessibility and influencing a broad array of areas, from cost savings to improved responsiveness.
There are numerous reasons to enable remote access for IoT devices. Consider the scenario where IoT devices are scattered across a wide geographic area or in locations where direct physical access is difficult or costly. Remote access eliminates the need for on-site visits for tasks such as configuration, troubleshooting, or software updates. This reduction in travel and physical intervention translates directly into cost savings and increased operational efficiency. Moreover, remote access enables faster response times in the event of issues. Instead of waiting for technicians to travel to the site, immediate attention can be given, which minimizes downtime and mitigates potential revenue losses.
Here's a table outlining some of the key benefits:
| Benefit | Description |
|---|---|
| Cost Reduction | Reduces the necessity for on-site maintenance and on-site visits |
| Increased Efficiency | Allows immediate attention to issues and fast turnaround times |
| Enhanced Security | Provides a controlled environment for remote management |
| Centralized Management | Facilitates management from a single location |
| Improved Scalability | Supports remote management of a large network of devices |
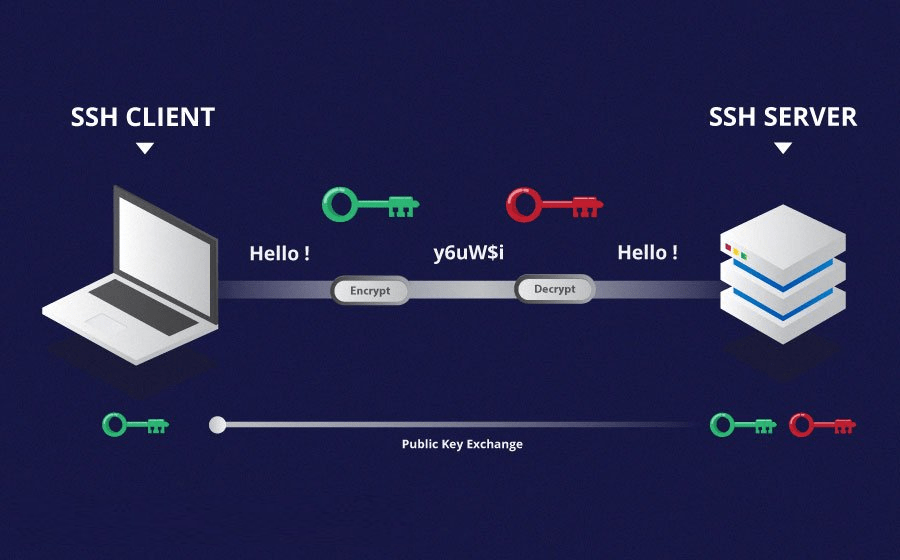
One of the core technologies for achieving this is SSH, or Secure Shell, which is a cryptographic network protocol designed to establish secure communication between a client and a server. It plays a critical role in providing a safe channel for remote access, ensuring that sensitive information, like login credentials, is protected during transmission. By using SSH, the risk of unauthorized access and data breaches are minimized.
In the context of IoT, SSH facilitates the secure exchange of data between the user and the IoT device, thus helping control and manage the device. It's essential to remember that the use of SSH on its own may not always be enough. Firewalls, network configurations, and the specific design of the IoT deployment can cause difficulties. To overcome these challenges, a number of techniques are used, one of the most important of which is the use of web-based SSH.
Web-based SSH provides an alternative to direct SSH connections, and is often easier to implement in many scenarios. A web-based system typically provides a user-friendly interface through a web browser, which allows remote control over the device. This can also remove the requirement for the users to install software on the local machine. This approach is particularly beneficial when dealing with diverse devices and user types, or when security considerations or device limitations hinder standard SSH setups.
Several platforms and software solutions provide web-based SSH access for IoT devices. They provide a user-friendly interface that hides the complexity of the underlying processes and also facilitates the management of multiple devices in an efficient and scalable way. Some of these solutions offer secure authentication, centralized management features, and real-time monitoring capabilities to improve the experience for the user.
Here are some methods to consider when looking into remote access to IoT devices, including web-based SSH options:
- Direct SSH: If the device is directly accessible over the network, this approach offers secure, command-line access.
- SSH Tunneling: Useful for accessing devices behind firewalls. It creates a secure tunnel for traffic. This can be achieved through a command-line or by using services.
- Web-Based SSH: Provides access to devices through a web browser. These solutions often include user-friendly interfaces and centralized management.
- VNC (Virtual Network Computing): For graphical user interface access, VNC allows users to view and control the device's desktop. This approach requires a VNC server on the device and a VNC client on the users end.
- Remote.it & Tailscale: These services provide secure access without needing to open firewall ports. They handle the complexity of network configurations and allow secure communication channels.
When it comes to accessing IoT devices behind a firewall, you're facing a common hurdle. A firewall is designed to block incoming traffic, which means a direct SSH connection into the device is typically not possible. In these situations, implementing SSH tunneling is an efficient approach, establishing a secure tunnel to bypass the firewall restrictions. This enables you to securely reach and manage your IoT devices even when they are behind a restrictive network barrier.
SSH tunneling can take different forms. For example, you might set up a TCP tunnel endpoint. This command sets up a secure channel through which all SSH traffic passes, allowing you to connect to the device. The remote IoT platform also enables users to remotely control IoT devices through a web browser. This method is helpful for those who don't want to install any additional software.
For those managing multiple devices or requiring simplified access, remote.it and Tailscale offer compelling solutions. Remote.it, for instance, provides secure SSH access without exposing devices to the internet. It simplifies firewall configurations and supports the management of diverse IoT devices.
Consider also the use of VNC server on a Raspberry Pi. With a VNC client application installed on the device of your choice, you can view and interact with the Pis desktop from any location with an internet connection. This is particularly useful if graphical access is needed. Remember, before setting up remote access, you must prepare the device for SSH access.
There are several practical steps to facilitate remote access. First, you must configure IP addresses and DNS settings. It is necessary to properly set up the devices IP addresses and DNS settings to enable remote access. This is particularly important if you're using static IP addresses.
Next, consider setting up a secure tunnel. Once the secure SSL/TLS tunnel is established, you can access your IoT device remotely using SSH. This ensures that all communication between the user and the device is encrypted, protecting sensitive information. This helps mitigate the chances of eavesdropping or data breaches.
Finally, consider the SocketXP web portal. Access the SocketXP web portal, and log in using your SSO login. Then, go to the devices tab and you can SSH into your IoT device. This portal also allows you to use the public web URL, which simplifies access to the device's web service from anywhere.
Here are some of the key steps to ensure secure and efficient remote access:
- Prepare the IoT Device: Ensure the device is ready for SSH access. This includes making sure the SSH server is running and configured.
- Configure IP Address and DNS: Correctly configure the IP address and DNS settings for remote connectivity.
- Set up a Secure Tunnel: Employ techniques like SSH tunneling or use services like Tailscale to create a secure connection.
- Use a Web Portal (SocketXP): Use tools like the SocketXP web portal to access the device through a web browser, streamlining the process.
- Secure Authentication: Always use strong passwords, enable two-factor authentication, and regularly review access logs.
- Regular Updates: Regularly update the device's firmware and software to ensure security patches are applied.
These are some of the best practices to keep in mind for security.
The benefits of the strategies we have discussed are numerous. Remote SSH access enables you to retain control, reduce downtime, and improve your IoT device management by eliminating the need to be physically present. This makes remote management not only possible but also practical and cost-effective.
In conclusion, the best remote IoT web SSH solutions offer a comprehensive approach to secure remote access, providing users with the tools they need to manage their IoT devices safely and efficiently. By understanding the basics, exploring the features, and implementing best practices, you can make informed decisions that benefit your business or personal projects. Whether you choose direct SSH access, web-based solutions, or services like Tailscale and remote.it, the key is to prioritize security and efficiency. Remote access for IoT devices is about ensuring control, simplifying management, and making your IoT ecosystem as robust as possible. With the right tools and techniques, you can transform your approach to IoT device management and create a safe and accessible digital environment.
As the digital world moves forward, secure and efficient remote access to IoT devices will continue to be a key element. As the need for such control grows, the solutions available will continue to evolve. Staying informed and updated on the latest technology and best practices will be vital to maintaining a secure and efficient digital world.