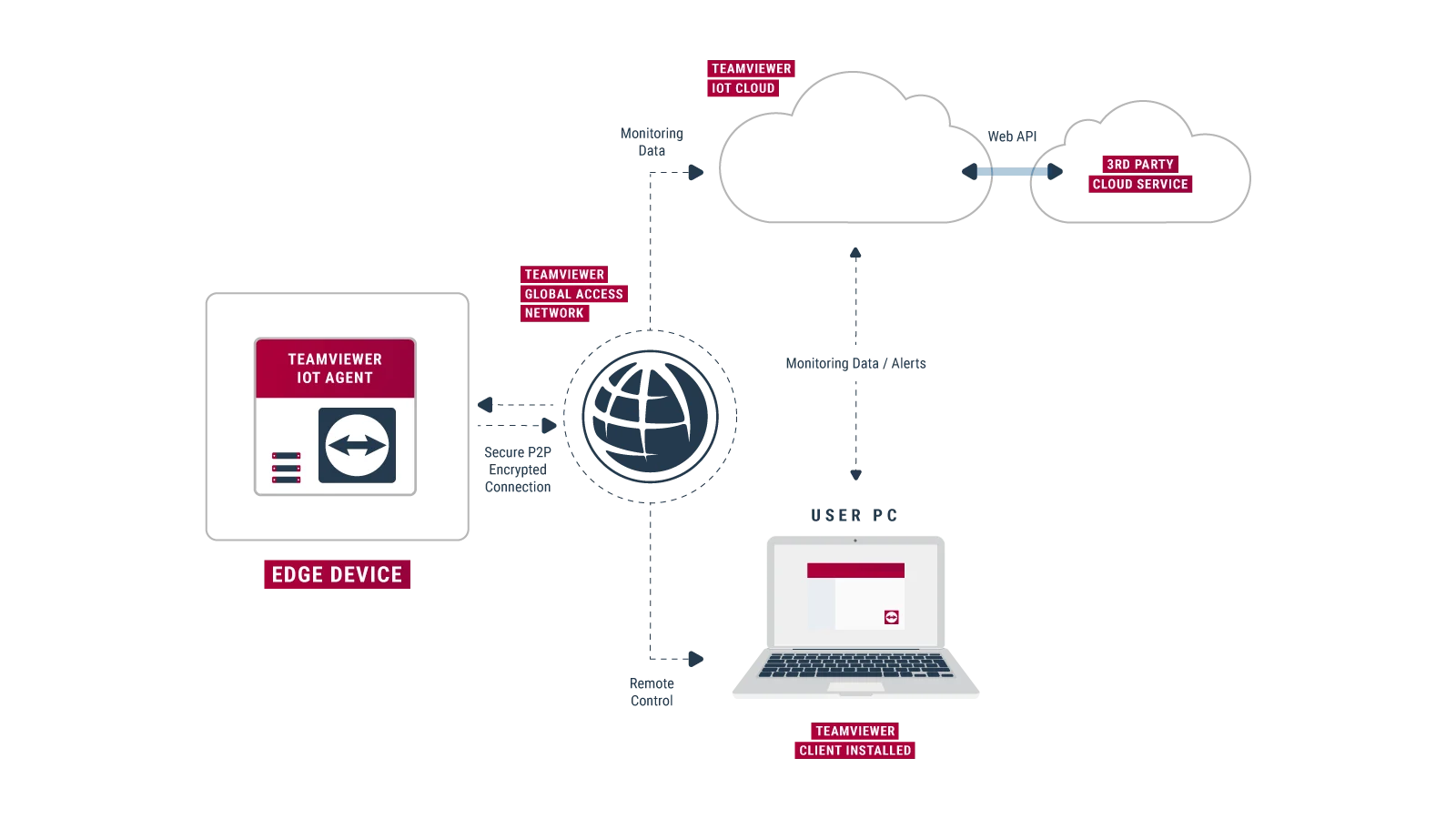
Can you truly unlock the potential of your Internet of Things (IoT) devices from anywhere in the world, without incurring hefty costs? The answer, remarkably, is yes, through the power of remote SSH login, offering a pathway to access and manage your IoT devices free of charge.
The digital world is rapidly evolving, and at the heart of this transformation lies the Internet of Things (IoT). This interconnected network of devices is reshaping how we interact with the physical world, from smart homes and retail spaces to industrial factories. IoT devices, by their very nature, are often deployed in distributed environments, making remote management not just a convenience, but a necessity. This is where the importance of remote access to IoT devices becomes apparent. The ability to monitor, control, and optimize these devices from a distance empowers us to harness their full potential. Whether it's a technician troubleshooting a sensor in a remote location or a homeowner adjusting the thermostat from a vacation, remote access is essential.
However, the challenge of accessing IoT devices remotely, especially without incurring significant expenses, can seem daunting. The good news is that several free tools and techniques provide a solution. One such method is remote SSH login, which offers a secure and reliable way to interact with IoT devices over the internet. This approach allows users to gain control over their devices from almost anywhere. The concept of free remote access to IoT devices may be difficult to accept, but it opens doors for better connectivity.
Let's delve deeper into understanding the essential aspects of remote SSH login for IoT devices, exploring its significance, benefits, and practical applications.
The core of IoT involves devices that collect data from the environment, and intermediate devices that connect these sensors to the internet. This seamless interaction enables the monitoring and control of various aspects of our lives and businesses. To remotely manage IoT devices effectively, several methods can be employed, including:
1. SSH (Secure Shell): This is a secure network protocol that provides a secure channel for accessing devices over an unsecured network. It's frequently used for remote command-line access and file transfer.
2. VPN (Virtual Private Network): VPNs create an encrypted connection over the internet, allowing secure access to your IoT devices from any location. This adds an extra layer of security when accessing devices over public or unsecured networks.
3. Remote Desktop Solutions: Software like SocketXP and others offer remote desktop access, allowing you to remotely control your IoT desktop from anywhere.
4. Cloud-Based Services: Platforms such as Amazon Web Services (AWS) offer various system management tools and remote service spaces to monitor and manage IoT devices.
5. TeamViewer IoT: This is available for free to monitor two IoT devices, providing a starting point for remote management.
When considering remote access solutions for IoT devices, the choice of method depends on the specific needs and security requirements. SSH is a good option for command-line access, while VPNs offer enhanced security. Remote desktop solutions provide a graphical user interface, and cloud-based services offer comprehensive management tools.
For those looking to remotely access a Linux server desktop from Windows over the internet, solutions like SocketXP can be employed. With SocketXP, you enter 'localhost' or '127.0.0.1' as the IP address and port 3000 on the RDC client to establish a connection. SocketXP also allows access from anywhere, using just a desktop or laptop computer to manage your IoT desktop remotely.
Moreover, it's important to note the role of cloud computing in the IoT landscape. Amazon Web Services (AWS) provides extensive cloud computing resources, including specialized modules like AWS IoT Device Monitoring. These services assist in managing, monitoring, and optimizing IoT devices within a scalable and secure cloud environment.
The application of IoT extends across multiple sectors, from logistics to smart homes and factories. In logistics, for example, IoT technology is expected to grow significantly, with an estimated CAGR of 13.2% between 2020 and 2030 in the global supply chain market, as per a newly conducted study.
The question then arises: why should you care about remote SSH login for IoT? Remote SSH login is important for several reasons:
- Convenience and Accessibility: It enables you to manage your IoT devices from anywhere with an internet connection.
- Cost-Effectiveness: SSH, especially when used in conjunction with free tools, can be a cost-effective solution.
- Security: SSH provides a secure connection, protecting your devices from unauthorized access.
- Control: You can monitor and control your devices as if you were sitting in front of them.
- Versatility: It can be used with various types of IoT devices and operating systems.
One of the most appealing aspects of remote SSH login is its accessibility. For the tech enthusiast or the beginner, this guide offers a step-by-step walkthrough of everything needed to implement remote SSH login for IoT devices for free.
To implement remote SSH login successfully, you will require:
- An IoT Device: This could be a Raspberry Pi, Arduino, or any device running an operating system that supports SSH.
- An Internet Connection: Both the IoT device and the device you'll be using to access it must have an internet connection.
- SSH Client: You'll need an SSH client on your computer. Common clients include PuTTY for Windows, and the built-in terminal for macOS and Linux.
- Static IP Address or Dynamic DNS: If your device's IP address changes, you'll need to use a dynamic DNS service to keep track of its location.
- A Router: You may need to configure your router to forward SSH traffic to your IoT device.
The steps involved in setting up remote SSH access typically include:
- Enabling SSH on your IoT device: This often involves installing an SSH server on the device.
- Configuring your router: This usually involves port forwarding so that external connections can reach your IoT device.
- Identifying your device's IP address: This can be a static IP address or one obtained using a dynamic DNS service.
- Connecting via SSH client: Using the client on your computer, you can enter the device's IP address or domain name to establish a secure connection.
The journey toward remote SSH login for IoT, however, must be approached with an understanding of the potential challenges that may arise. Network configurations, security protocols, and the ever-changing landscape of the internet can present difficulties. It's important to remember, in the face of these complexities, that the benefits of remote access are significant.
It's also worth mentioning the role of free remote PC software trials. These tools can offer an easier approach for remote access, particularly in corporate environments, though their features may be limited compared to paid solutions.
When you venture into remote access, security is a crucial consideration. Using a VPN adds an extra layer of security. A VPN creates an encrypted tunnel, protecting your data from interception. It also allows you to access your IoT device from anywhere in the world, as long as you have an internet connection. Whether in a different country or on the move, you can manage and monitor your device. Remember to be careful when accessing your IoT device over public or unsecured networks.
Another important aspect is the use of remote desktop solutions like SocketXP. These solutions enable users to bypass the command line interface and enjoy a familiar desktop environment on their IoT device. With remote desktop access, you have full control over your IoT device, just as if you were sitting in front of it. Using SocketXP, you can access your IoT desktop remotely from anywhere using a desktop or laptop computer.
In summary, remote SSH login for IoT offers a robust, flexible, and often cost-effective method for managing IoT devices. As more devices enter the world of the Internet of Things, the significance of remote access only continues to grow. For tech enthusiasts and professionals, mastering this concept can unlock numerous possibilities for managing and monitoring devices from anywhere in the world.