Is securing your Internet of Things (IoT) devices a complex puzzle you're struggling to solve? The ability to securely and efficiently manage IoT devices remotely is not just a convenience, it's a necessity in today's interconnected world.
The proliferation of IoT devices, from smart home appliances to industrial sensors, has created unprecedented opportunities for data collection, automation, and efficiency gains. However, this growth has also introduced significant security challenges. Ensuring the confidentiality, integrity, and availability of data transmitted by and to these devices is paramount. Remote access, while crucial for maintenance, updates, and troubleshooting, opens up potential vulnerabilities that malicious actors could exploit. This necessitates the implementation of robust security measures and protocols to protect against unauthorized access, data breaches, and other cyber threats. The evolution of IoT security is closely linked to the development of secure remote access technologies. This is driven by the need to maintain control and oversight of devices deployed in diverse and often physically inaccessible locations. Effective remote access solutions provide a secure channel for communication, enabling administrators to monitor device health, update firmware, and respond to alerts without physically visiting each device. These solutions must adhere to rigorous security standards to prevent unauthorized access, which could have catastrophic consequences.
Consider the scope of the challenge: over 10 billion IoT devices were connected globally in 2021, and that number is projected to explode to over 25 billion in the coming years. This growth represents a massive attack surface for cybercriminals. Each device, from a seemingly innocuous smart light bulb to a critical industrial control system, represents a potential entry point. A compromised IoT device can be used to steal sensitive data, launch attacks on other devices, or even disrupt critical infrastructure. Therefore, implementing a strong security posture is non-negotiable, encompassing not just remote access protocols but also device authentication, data encryption, and regular security audits.
The cornerstone of secure remote access for IoT lies in the implementation of strong authentication mechanisms. This ensures that only authorized users and devices are granted access to the network and its resources. This can involve multi-factor authentication (MFA), which requires users to provide multiple forms of identification, such as a password and a one-time code generated by an authenticator app. In addition to robust authentication protocols, encrypting all data transmitted between the IoT device and the access point is crucial. Encryption transforms data into an unreadable format, making it useless to unauthorized parties who intercept it. Protocols such as SSL/TLS provide this crucial security layer, preventing eavesdropping and data tampering. Further strengthening security requires implementing regular security audits and vulnerability assessments. These assessments proactively identify potential weaknesses in the system before they can be exploited by attackers. Regular audits ensure that security protocols are functioning correctly and that the system is compliant with relevant industry standards.
Many solutions exist for securing remote access to IoT devices. Cloud-based platforms, such as SocketXP, offer secure remote access solutions to manage embedded Linux devices and other IoT devices over the internet. These platforms create a secure SSL/TLS connection to the device, enabling administrators to securely access and manage the device remotely. Other options include the use of VPNs (Virtual Private Networks) specifically tailored for IoT devices. However, it is important to acknowledge that VPNs tailored for IoT devices are, in fact, quite rare. An alternative approach involves using SSH tunnels to bypass firewall restrictions and gain secure access to the IoT device. AWS IoT device management supports the creation of a device tunnela secure remote SSH session to a device installed behind a restricted firewall.
The importance of security in the IoT landscape cant be overstated. As the IoT ecosystem expands, securing networking solutions becomes increasingly important. The inherent vulnerability of these devices demands that robust security measures are implemented at every stage. The cost of neglecting security can be catastrophic, leading to data breaches, operational disruptions, and reputational damage. The key is to approach security with a proactive, layered strategy. This includes robust authentication, encryption, regular security audits, and the adoption of appropriate security tools and protocols. The ever-evolving threat landscape necessitates constant vigilance and continuous improvement in security practices. The future of IoT depends on the industrys ability to address and overcome its security challenges.
The initial steps in connecting an IoT device to the network require a secure process. The IoT device initiates the connection, and the server authenticates the user or device to prevent unauthorized access. This secure authentication process is critical to safeguard the network from malicious attacks. When an IoT device attempts to connect, the process unfolds through several crucial secure steps: authentication, which verifies the devices identity, and encryption, which protects data in transit. This process must be robust and implemented diligently to maintain the integrity of the IoT network.
Moreover, the concept of secure remote access extends beyond simple connectivity. It encompasses a holistic approach to device management. Remote monitoring, centralized management, and the ability to monitor distributed devices efficiently are all fundamental. Effective solutions must offer value for money, providing robust capabilities at a reasonable cost. This means investing in a tool that provides remote monitoring capabilities, enables centralized management, and is affordable. This is crucial to maximizing return on investment while ensuring devices remain secure and manageable.
Managing IoT devices remotely in the era of the internet of things presents both opportunities and challenges. Systems have the ability to utilize analytics and business intelligence far faster and better than a human being. Therefore, the systems deployed must be able to manage this complex environment while mitigating associated risks. In practical terms, this can involve the use of a device management platform that supports functions such as remote configuration, firmware updates, and diagnostics. This ensures that devices are running the latest software, configured correctly, and can be quickly troubleshooted if issues arise. Effective device management is crucial for maintaining operational efficiency and minimizing downtime.
The underlying architecture of IoT networks can be quite complex. However, the ability to build secure, fast, and scalable IoT networks requires more attention. This involves careful planning, design, and implementation. This includes factors such as network segmentation, access controls, and security protocols. Because IoT networks are becoming more complex, choosing appropriate security solutions that can scale with the network's growth is very important. This will help ensure optimal performance and maintain security as the ecosystem expands.
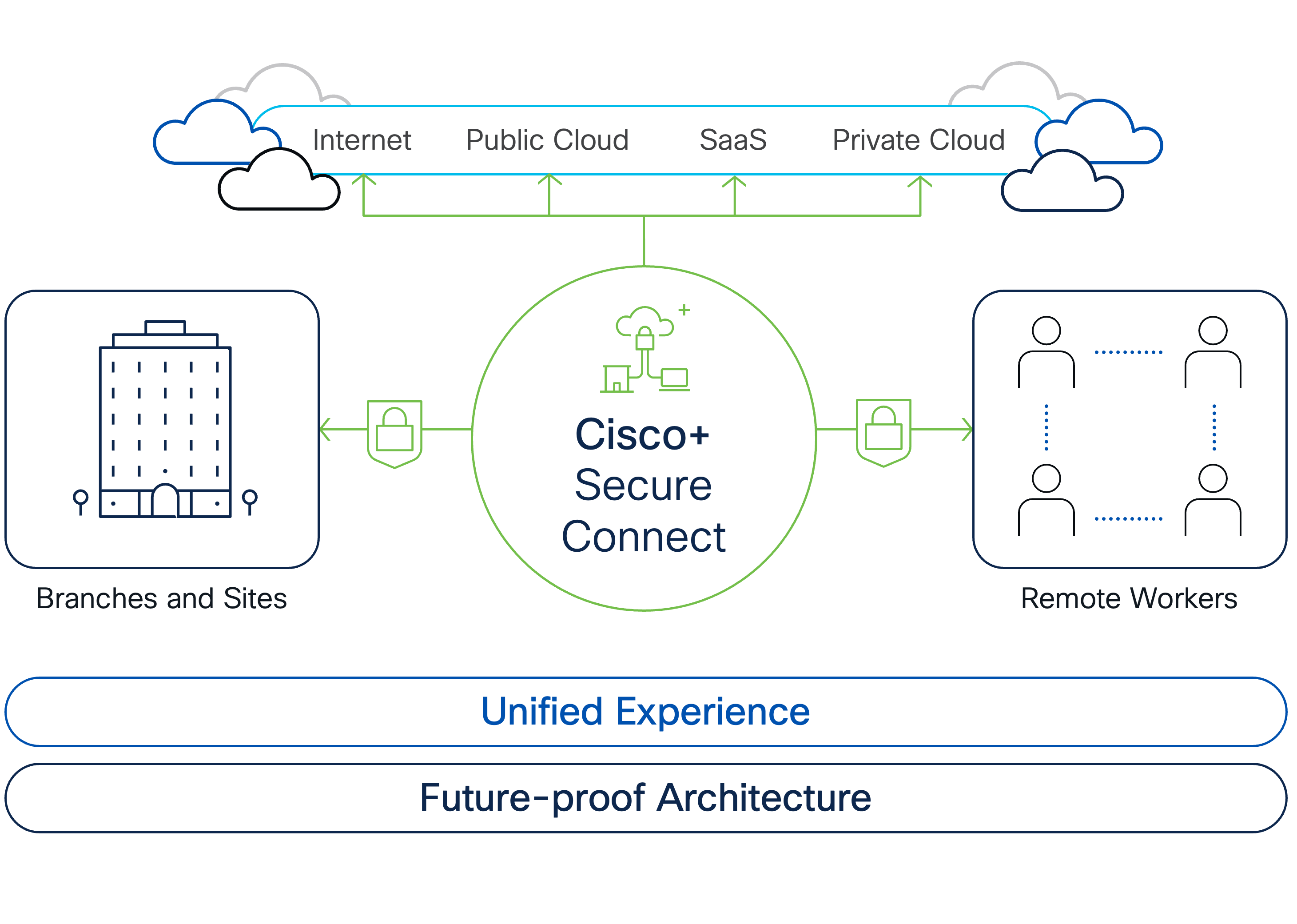
The use of technologies such as Cisco Secure Access Service Edge (SASE) with Cisco Secure Connect offers a robust framework for securing remote access. This design provides a reference for implementation details, incorporating additional security capabilities such as Cisco Duo, Cisco Secure Client (AnyConnect), and Cisco ThousandEyes. The validated design ensures that best practices are followed and provides a trusted foundation for securing remote access to IoT devices.
When considering remote access solutions, keep in mind that some offer additional advantages. These advantages include the ease of setup, minimal configuration, and flexibility. For instance, no port forwarding or complex VPNs are needed to use solutions like the one provided by SocketXP. This greatly simplifies the process of enabling secure remote access while minimizing the potential for configuration errors.
In the realm of secure remote access, understanding the steps to connect IoT devices to the cloud is essential. These steps often involve secure communication protocols, device authentication, and data encryption. The process may differ slightly based on the chosen cloud platform. Understanding these steps is key to implementing a successful and secure cloud integration. By following these steps carefully, businesses can leverage the power of the cloud while maintaining the security of their IoT devices.
The challenges of securing IoT devices are complex. However, by staying informed about the latest threats, adopting best practices, and deploying the right tools, businesses can protect their assets and realize the full potential of the IoT. The goal is to build a secure, scalable, and manageable IoT ecosystem. The focus should be on the development of comprehensive strategies and solutions. It's important to proactively address potential vulnerabilities. This helps organizations navigate the evolving landscape of IoT security.