In an era where the Internet of Things (IoT) is rapidly transforming how we live and work, have you ever considered the critical role of secure remote access in managing these ubiquitous devices? The ability to securely connect to and manage your IoT devices from anywhere in the world is no longer a luxury, but an absolute necessity for maintaining operational efficiency, safeguarding sensitive data, and ensuring the integrity of your entire IoT ecosystem.
The proliferation of IoT devices, from smart home appliances to industrial sensors, has created an unprecedented demand for robust and secure remote management solutions. This is where Secure Shell (SSH) technology comes into play, offering a secure and reliable means of accessing and controlling your IoT devices remotely. SSH acts as a secure channel, encrypting the data transmitted between your device and your remote access point, thereby preventing unauthorized access and data breaches. Moreover, SSH facilitates a myriad of essential functions, including troubleshooting, firmware updates, configuration management, and continuous monitoring.
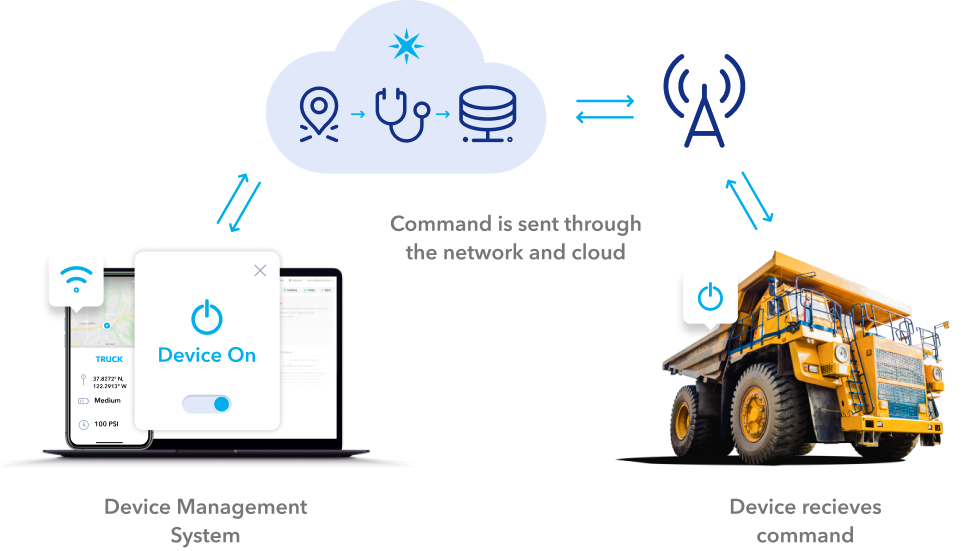
The essence of remote IoT management lies in the ability to access and control devices irrespective of their physical location. This capability is achieved through a variety of methods, with SSH being a preferred choice due to its secure nature. The beauty of SSH lies in its versatility. Whether you're a developer, network administrator, or IT professional, the ability to manage remote IoT devices through SSH is crucial for maintaining secure and efficient operations. This includes not only the initial setup and configuration but also ongoing maintenance and proactive monitoring, enabling you to respond promptly to any issues and keep your IoT infrastructure running smoothly.
One of the most effective ways to secure your IoT devices is through the use of P2P SSH, particularly on devices like the Raspberry Pi. This approach establishes a secure, encrypted tunnel for communication, safeguarding sensitive data and ensuring the integrity of your IoT ecosystem. By downloading free SSH tools and adhering to best practices, you can build a robust system for managing your devices. This is especially critical given the inherent vulnerabilities that come with interconnected devices. Protecting against potential threats requires diligence in employing robust security measures.
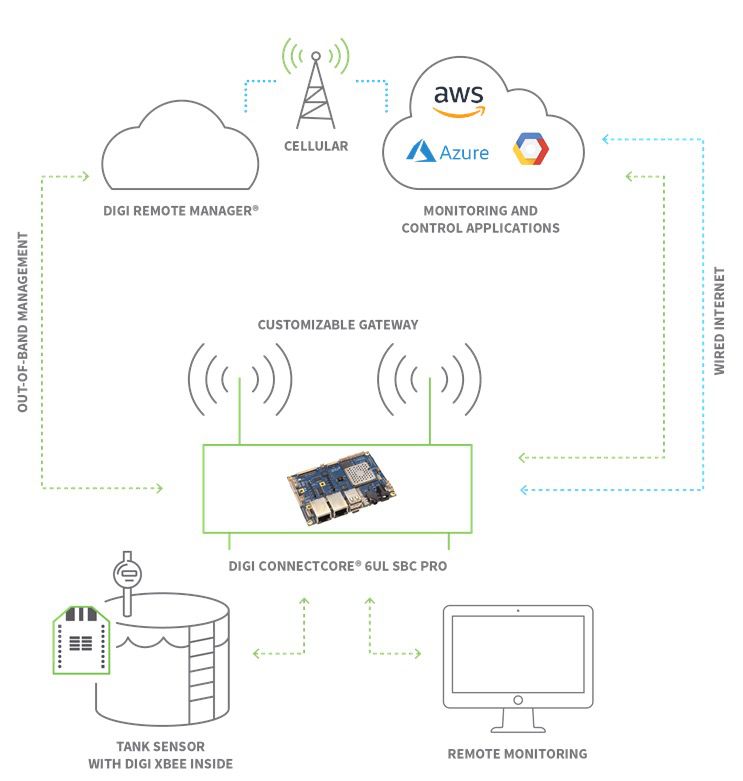
The Remoteiot platform SSH provides a robust solution for managing remote IoT devices and servers securely. Secure shell (SSH) is a protocol that provides a secure channel over an unsecured network, and it plays a vital role in managing IoT devices remotely. Now you can access your IoT devices SSH server using a local endpoint, instead of a public endpoint. With the rise of IoT technology, the need for secure and efficient remote management systems has never been more critical. Remote IoT VPC SSH download plays a pivotal role in securely accessing and managing IoT devices across virtual private clouds (VPCs).
One powerful tool in this domain is IoT remote SSH download, which enables secure and efficient access to IoT devices from anywhere in the world. Whether you're troubleshooting, updating firmware, or managing configurations, SSH provides a reliable and encrypted way to interact with your IoT devices. If you're looking to download and configure SSH for remote access on your Mac, this guide will walk you through everything you need to know.
Whether you're a beginner or an advanced user, understanding how to set up and use SSH for IoT devices on Mac can significantly enhance your productivity. Remote SSH access is essential for IoT device management, enabling administrators to troubleshoot, configure, and monitor devices from anywhere in the world. IoT remote access refers to the ability to access and control an IoT from a remote computer or device. This can be done using a variety of methods, such as SSH, VNC, and RDP.
Remote access to an IoT can be useful for a variety of purposes, such as maintenance, data collection, and control. With IoT devices popping up everywherefrom healthcare to manufacturingthe demand for secure, efficient remote access solutions has skyrocketed. Socketxp is a cloud-based IoT device management and remote access platform. Remotely manage, access, and monitor your IoT devices, Raspberry Pi fleet, or any Linux machines behind a NAT router and firewall.
SSH ensures that data has not been tampered with during transmission. By securely connecting remote IoT devices, organizations can streamline operations, reduce costs, and improve efficiency. Linux and IoT device management made easy. Take full control of your Ubuntu Linux machine with our comprehensive guide to SSH remote access without port forwarding. Unlock the power of your Ubuntu Linux server from anywhere, anytime with our expert tips and tricks.
Following the steps to set up a platform and remote SSH into your IoT using a remote access solution is crucial. You can download and install an agent on your IoT device from there.
For those working with Raspberry Pi, this often involves utilizing standard client tools like PuTTY and configuring the system for secure authentication using SSH keys. This ensures that the communication channel is not only encrypted, but also that only authorized individuals can access the device. When setting up an IoT device on a Raspberry Pi, several measures can be undertaken to ensure its security. Starting with a strong, unique password for the user account is essential.
Furthermore, regular updates of the Raspberry Pi's operating system are crucial to address any potential security vulnerabilities that may arise. Another critical element is understanding how to configure the SSH service to disable password-based login, and instead, solely rely on SSH key-based authentication. This significantly enhances the security of your device by preventing brute-force attacks. Implementing these measures ensures a secure and robust environment for your IoT devices, protecting them from unauthorized access and potential threats.
The adoption of IoT technology is accompanied by several security concerns that must be addressed. Given the sensitive nature of data handled by IoT devices, such as in healthcare or financial systems, it's imperative to safeguard against potential threats. This is where the concept of end-to-end encryption becomes crucial. By encrypting data at the source and decrypting it only at the destination, you ensure that even if the data is intercepted, it remains unreadable to unauthorized parties. This method of protecting data is a key factor in security.
With the rise of remote work, the need to securely access IoT devices from anywhere has become more important. The concept of tunneling or VPNs is an essential aspect of remote IoT security. By creating an encrypted tunnel for all network traffic, a secure path is created for communications, even across untrusted networks. This ensures that data exchanged is private and secure. The use of VPNs provides an extra layer of security by encrypting all data traffic that passes through the connection. This makes it significantly more difficult for attackers to intercept and read data.
Furthermore, the establishment of a strong and reliable remote management system is critical for the long-term security and functionality of IoT devices. By implementing such systems, security patches and firmware updates can be applied to the devices. This is crucial for patching vulnerabilities before they can be exploited. In addition, the use of a remote management system allows for central monitoring, enabling the rapid identification and mitigation of any security breaches or operational issues. Ultimately, investing in a robust remote management system provides an added defense and strengthens the overall security posture of your IoT infrastructure.
The use of SSH keys is critical for securing remote IoT connections. SSH key-based authentication is considered more secure than passwords because it eliminates the risk of password guessing and protects against brute-force attacks. By generating and using a unique SSH key pair, the private key is kept secret, while the public key is installed on the IoT device. The device grants access only to those users who possess the corresponding private key, preventing unauthorized access.
The combination of SSH and other security protocols, such as TLS, creates a robust security framework that protects your IoT devices from potential threats. TLS encrypts the data in transit, ensuring that only authorized parties can read and understand the information being exchanged. By incorporating both SSH and TLS, you ensure a defense-in-depth approach that protects all aspects of the IoT communication chain.
The benefits of securing remote IoT connections are substantial. By implementing robust security measures, you not only protect the integrity and confidentiality of the data handled by the devices, but you also ensure that operations can continue without interruption, and compliance with industry regulations is maintained. Moreover, security is essential for establishing and maintaining trust between you and your customers. By creating a secure environment, it promotes confidence in your devices and helps to reduce the risk of reputational damage. This level of trust is essential in many applications, especially in highly regulated sectors.
When considering remote IoT connections, it's critical to have a well-defined security policy. This is a set of guidelines that govern how your devices are secured and how data is managed. This policy should cover aspects such as password management, access controls, and data encryption. It should be regularly reviewed and updated to reflect changes in threats. By documenting and adhering to a security policy, you create a framework that supports secure operations, while promoting compliance.
One of the often-overlooked aspects of IoT security is the physical security of the devices themselves. This includes protecting devices from physical tampering and unauthorized access. The environment where the devices are placed plays an important role, ensuring that they're kept in a secure location that's protected from potential threats. For example, you might consider placing devices in locked cabinets or securing them to prevent theft. Combining physical security with other cybersecurity methods will provide a comprehensive approach to IoT security.
Security is a continuous process, and that requires ongoing monitoring and assessment. This includes regularly reviewing and updating your security measures, conducting vulnerability scans, and monitoring network traffic for any signs of malicious activity. Additionally, incident response plans should be established to be prepared for any security breaches. Regular security checks are also crucial for ensuring that your IoT infrastructure remains secure. This means that security is not a one-time task, but an ongoing commitment that is required.
The future of IoT security is likely to involve even more robust security measures, including the increased use of artificial intelligence and machine learning to detect and respond to threats. This is the most promising development in cybersecurity that involves the adoption of AI-powered tools. These tools can analyze large amounts of data to identify patterns and anomalies, and automatically respond to potential threats. Furthermore, as IoT devices become more connected and complex, the need for advanced security solutions will only continue to grow, making it essential to stay informed about new developments in the field. As IoT becomes even more interconnected and complex, the need for more advanced security solutions will grow.
In the rapidly evolving landscape of IoT, securing remote access is no longer an option but an absolute necessity. Implementing strong security measures and being constantly vigilant are the most effective ways to ensure that your IoT devices are protected against existing and emerging threats. By prioritizing security at every level of your IoT ecosystem, you can unlock the full potential of this technology while minimizing the risks. By staying proactive and informed, you can safeguard your devices and data, and keep the benefits of the IoT world.